Auto-Merging Dependabot Pull Requests
There are few things less fun than keeping all of my websites' dependencies up to date. About a year ago, I added Dependabot to my personal projects...
Dependabot pulls down your dependency files and looks for any outdated or insecure requirements. If any of your dependencies are out-of-date, Dependabot opens individual pull requests to update each one.
This made the process way easier. Thanks to Vercel for GitHub, all of my pull requests included a preview URL where I could verify everything was working as expected before I merged my changes. So at this point, I'd open the preview URL, verify everything looked good, and click the merge button.
I was feeling great! ... But then Brian Lovin suggested a way to make it even better.
Add some tests + auto merging + auto deploying and put that on autopilot 🚀
— Brian Lovin (@brian_lovin) December 13, 2019
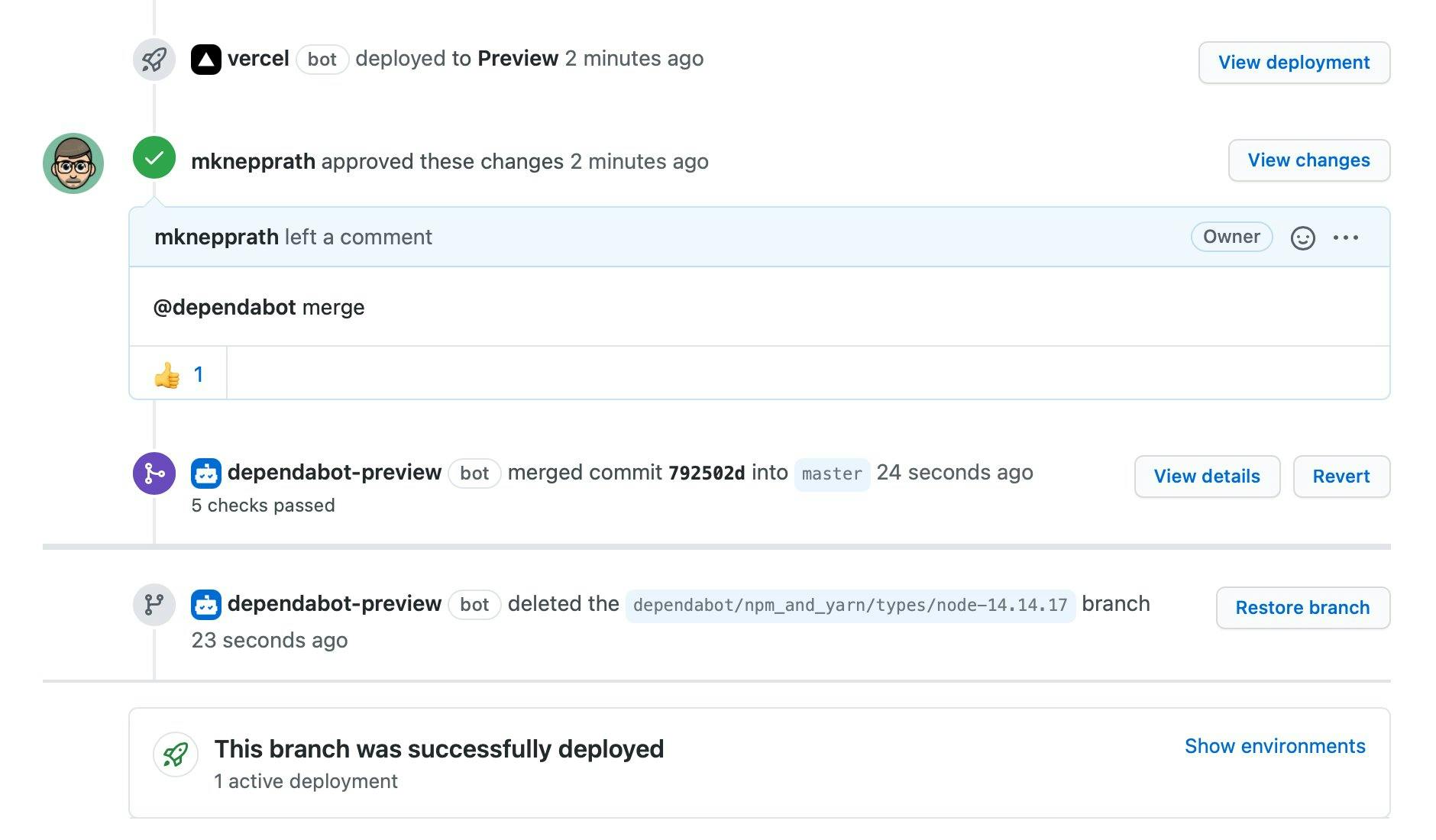
A year later, I was nearing the end of 2020 with a huge backlog of PRs. Despite how easy I had made it for myself, it was still a pain to verify and merge all of them one at a time. I decided to give Brian's suggestion a shot.
Add Some Tests
First problem: I had zero tests.
When manually checking Vercel's preview URL, I'd typically verify a few things, but for the most part, I'd just check to make sure my site loaded up successfully.
I decided to set up some tests with Cypress to check this instead. Most of the tests simply verify that the pages load - but some also check the content to make sure it's loading in a way I'd expect.
I then followed a guide to add the Cypress GitHub Action to run these tests on every commit to GitHub. This was the first GitHub Action I ever implemented!
Auto-Merging
Now, the fun part.
I had a lot of issues finding a GitHub Action that would work for me. While researching this, I discovered it was a feature that had been removed from Dependabot post-GitHub acquisition. GitHub's reasoning:
If we enabled GitHub Actions to push to a protected branch then any collaborator in your repo could push any code to any branch they wanted simply by creating a branch and coding the workflow to push to some other branch.
If you want to push to a protected branch, you have to have explicit permission to push to that branch. Bots not excluded.
I spent some time trying to figure out how to give Dependabot push access to no avail. I did find a different workaround, however. Instead of giving push access to the bot, I set up the automation using an account that already had push access. Mine.
You can check out this GitHub Action here.
After tweeting about this issue, Florian Fittschen suggested another (probably better) solution: using a GitHub Action to generate the token. I haven't tried this yet, but I'd recommend looking into this for future auto-merge workflows.
Autopilot
This worked so well, I quickly added these same GitHub Actions to all of my other sites. Updates and security patches are now submitted, tested, merged, and deployed without any hand-holding from me - all I see are the merge notifications after the fact. Nice!
Copied that action over to a couple of my repos yesterday, can't wait for the automerge magic to begin!
— Brian Lovin (@brian_lovin) January 5, 2021